Store Hours: Monday to Friday - 8:00 to 5:30 - Closed Saturday & Sunday |
Tech Topics:
Current Topic:
Potential Fire Hazard
Past Topics:
Be Alert When Installing Software
Protect Your Mobile Devices
CryptoLocker
Safer Internet Day
The Microsoft Phone Support Scam |
|
Potential Fire Hazard:

|
Desktop computers built between 2008 and 2012 may be at risk of catching on fire!
ATX molex to SATA power adapters are/were used in computers that have/had no or too few SATA power connections available from the internal power supply. It has come to our attention that some of these adapter cables are made of plastic that degrades over time and becomes electrically-conductive. This leads to heat build up, melting and possible flame.
Damage may be limited to the adapter cable itself, or may spread to the connected hardware, the entire computer chassis, or even spread outside of the computer.
The adapter cable is common throughout the industry and may have been used in many makes and models of computer system.
If you are at all concerned that your desktop computer may be at risk, bring it in to Georgian Bay Software and we will check it while you wait. |
Be Alert When Installing Software:
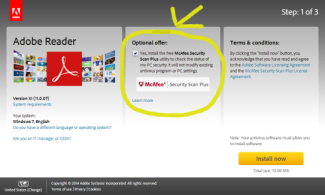
Click here to see more examples
|
There is a lot of great software available to download from the web - much of it for free. But, computer users often fall into the trap of clicking 'Next' / 'Accept' / 'Agree', too quickly.
Taking a second to review, before clicking, helps users avoid inviting in malware, spyware and ad-ware.
Even if the 'Special Offer' or 'Optional Offer' is not malicious (as in the image on the left), it may still be unwanted and/or unneeded.
The majority of the time, the check boxes are pre-checked or the option to decline is not obvious. But users can be alert when installing software and their computers will run more quickly and smoothly.
|
|
Protect Your Mobile Devices:



|
The same threats that are a problem for PCs/MACs – viruses, malware and identity theft - are also threats to your smartphones, tablets and other mobile device(s).
Georgian Bay Software is your

Coming soon

|
|
CryptoLocker:
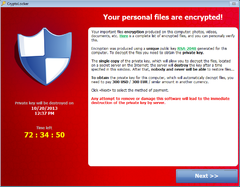
From Wikipedia, the free encyclopedia |
CryptoLocker is a ransomware trojan which targets computers running Microsoft Windows and first surfaced in September 2013. A CryptoLocker attack may come from various sources; one such is disguised as a legitimate email attachment. When activated, the malware encrypts files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displays a message which offers to decrypt the data if a payment (through either Bitcoin or a pre-paid voucher) is made by a stated deadline, and threatens to delete the private key if the deadline passes. If the deadline is not met, the malware offers to decrypt data via an online service provided by the malware's operators, for a significantly higher price in Bitcoin. Payment often, but not always, has been followed by files being decrypted.
Although CryptoLocker itself is readily removed, files remain encrypted.
Contact us for Virus Removal and Data Backup solutions!
A safe, reliable Back Up System is key. |
|

|
Every February, countries and organizations around the globe promote safer and more responsible use of online technology and mobile phones, especially amongst children and young people across the world. Click here to learn more. |
|
The Microsoft Support Scam:
The scenario: You receive a phone call from someone claiming to be a Microsoft Support Technician. They have detected that you are having problems with your computer and are calling to help you solve them. They will ask you to check a few settings on your system to verify what they believe is the problem, and will be very convincing. When questioned, they may claim that Windows automatically reports errors to Microsoft and they were simply following up on those automated reports. Once they have you believing that they have the right system, and the right problem, they will get you to go to a web site which will run a tool that will let them take control of your system so that they can "fix" the issue.
At this point, there are several variations of what may occur - In almost all cases they will proceed to poke around in your system as you watch - making it look like they are changing settings and generally fixing things and then they will then ask you for a credit card to pay a "reasonable" fee for the service. More often than not, they will have installed some form of malware on the system as well. This is software which is designed to either redirect your search results to sites of the scammer's choosing, or to make your computer part of a "Bot-Net" to be used by the scammer/hacker in the future.
Things to remember: First and foremost, Microsoft will NEVER contact you unsolicited for tech support. Second,
What to do if this has already happened to you: If you think that you might have downloaded malware from a phone tech support scam web site or allowed a cyber-criminal to access your computer, take these steps:
- Change your computer's password, change the password on your main email account, and change the password for any financial accounts, especially your bank and credit card.
- Scan your computer with a trusted Anti Virus program to find out if you have malware installed on your computer. If you are still unsure, bring your computer to a trusted computer repair shop to have them test it for malware and/or clean it.
|
Stay Tuned! We will be tackling more of today's most common computer-related topics - sharing advice and tips to help you make the most of your computing experience.

|
Copyright © 2014 Georgian Bay Software | All Rights Reserved |
|





